

Your office reception security isn't just about checking IDs and handing out badges anymore. It's the first line of defence protecting your people, assets, and reputation. Every single person who walks through your front door is either an opportunity or a threat.
But here's the good news! Modern office reception security doesn't require a fortress mentality. The right combination of clear policies, smart technology, and well-trained staff creates security that's both effective and welcoming.
Visitor management systems and other digital tools certainly help, but they're enablers, not silver bullets. The foundation remains your documented procedures, trained personnel, and commitment to consistent enforcement. Let's walk through ten practical approaches that address reception security challenges in 2026.
1. Design the Visitor Journey & Written Reception Policy
Before you deploy any technology or hire security staff, map out exactly what happens when someone walks through your door.
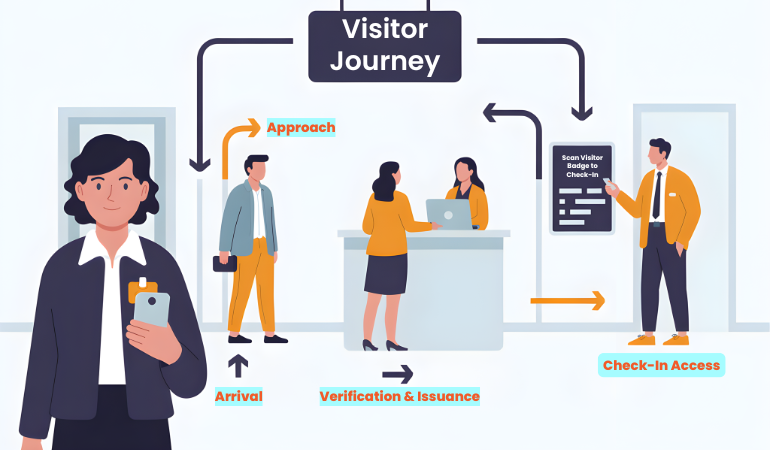
Start with visitor journey mapping. Document every single touchpoint:
- Arrival at the building entrance
- Approach to the reception desk
- Identity verification and check-in
- Badge issuance
- Escort or independent access
- Visit duration
- Check-out process
- Badge return and exit
When you map the complete visitor check-in flow, you'll spot gaps. Maybe there's a side door that bypasses reception. Perhaps visitors can wander to the elevator before anyone verifies their appointment.
Next, define your visitor categories policy. Not everyone who enters your building needs the same treatment:
- Regular visitors: Clients, partners, and frequent consultants who visit often.
- Contractors: Maintenance staff, construction workers, IT technicians with extended access needs.
- Delivery personnel: Package couriers who need quick in-and-out access.
- VIP guests: Executive visitors requiring discretion and streamlined entry.
- Walk-ins: Unscheduled visitors who require additional scrutiny.
Each category should have documented procedures. Your visitor management policy needs to specify exactly what information you collect, who has authority to approve access, and what to do when someone doesn't fit the expected profile.
Then draft a Front Desk SOP Template that covers these scenarios:
- Who checks identification and what forms are acceptable.
- What visitor data you collect (and your legal basis for collecting it).
- Visitor escalation policy for denied access or suspicious behaviour.
- Emergency contact procedures.
- Badge types and access levels for each visitor category.
Finally, display your reception signage policy prominently. Visitors should see clear instructions about check-in requirements before they reach your desk. Transparency builds trust and sets expectations immediately.
Start Your Free Trial Today
Experience all the amazing functionalities of VizMan with our 14-day free trial. No commitment, full access to all features.
Register Now
2. Pre-Registration & Appointment Verification
Visitor pre-registration transforms your reception from reactive to proactive. When employees pre-register visitors through your system, you're not scrambling to verify credentials when someone shows up unexpectedly.

Here's how guest pre-registration systems work in practice:
Your employee schedules a meeting and enters visitor details into the system. The system automatically sends the guest an appointment confirmation SMS or email with the meeting time, location, host name, and any access instructions. Most systems now generate a pre-registration QR code that the visitor can scan at a kiosk for instant entry.
The difference between pre-scheduled visitors and walk-ins is substantial. Pre-registered guests move through check-in in under 60 seconds. Walk-ins require phone calls, email confirmations, and manual data entry that takes 3-5 minutes and creates queues.
3. Contactless & Self-Serve Check-In (QR / Kiosks)
Contactless visitor management has evolved from temporary solution to operational standard. The efficiency gains and reduced reception workload make touchless visitor check-in the baseline expectation in 2026.
Deploy a self-service visitor kiosk in your lobby. These kiosk check-in systems let visitors handle their own registration while your reception staff focuses on exceptions and hospitality.
The process is simple: a visitor approaches the kiosk, enters their name or scans their QR code, confirms their appointment details, has their photo taken, and receives a printed or digital visitor badge. Total time: 45 seconds.
But here's the critical part: always provide fall-back options. Not every visitor is comfortable with technology. Your kiosk visitor registration system should have a clear "Need Help?" button that summons a staff member. Keep a manual check-in option available for elderly visitors, those with disabilities, or anyone who simply prefers human interaction.
4. Identity Verification & ID Scanning
Visitor ID verification is non-negotiable for secure facilities, and increasingly standard even in casual office environments. The question isn't whether to verify identity, but how to do it efficiently and respectfully.
Modern ID scanning for visitors takes seconds. Your receptionist (or self-service kiosk) uses a scanner or ID verification software to capture information from government-issued IDs. The system reads the magnetic strip or barcode, extracts name, photo, date of birth, and ID number, then populates your visitor log automatically.
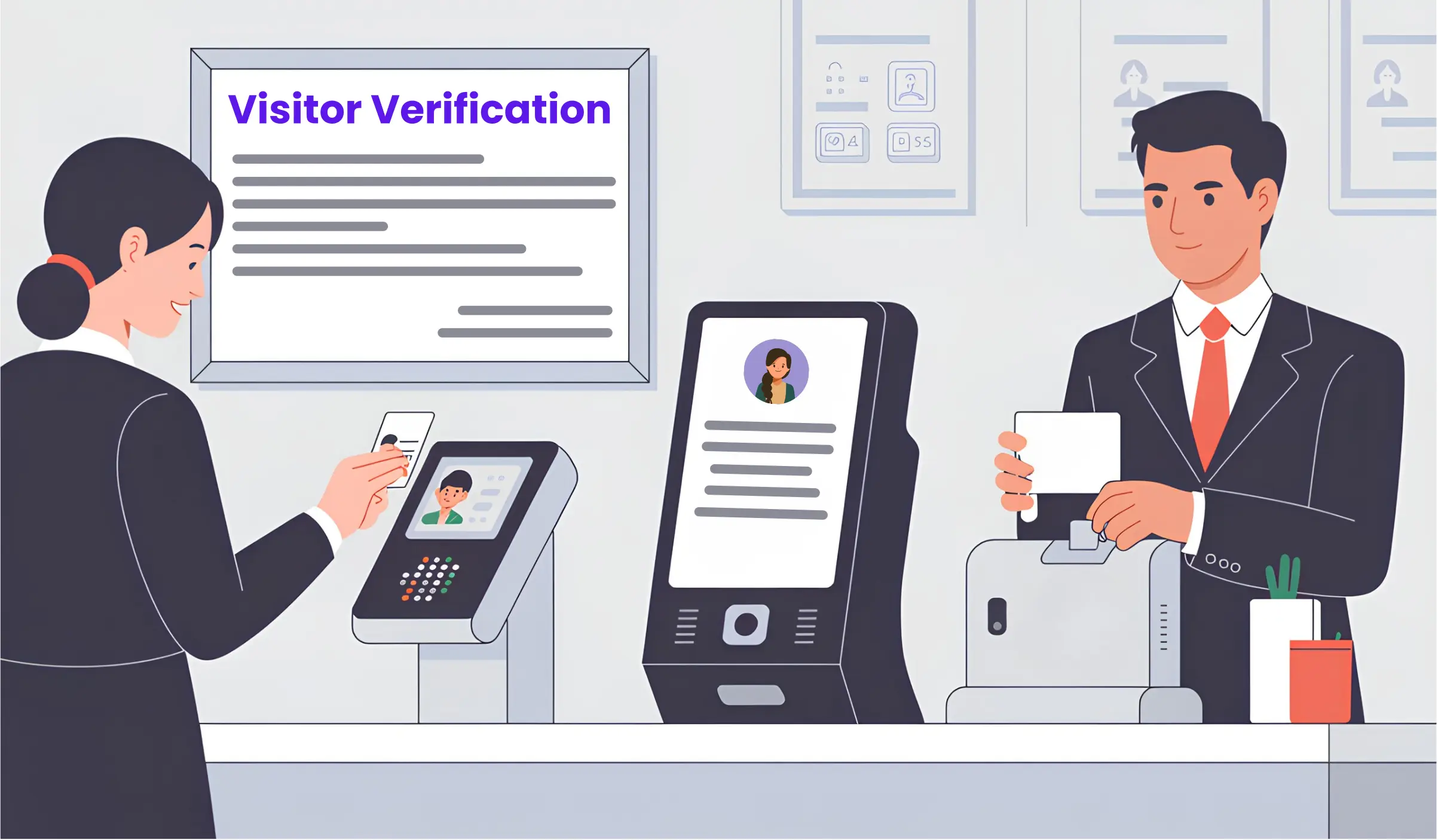
The benefits extend beyond security. ID scanning kiosk systems with badge printing capabilities can create professional visitor badges in one continuous workflow. Scan ID, capture photo, print badge with name and photo, all in under 30 seconds.
Some organizations use biometric visitor verification. Facial recognition can flag when someone attempts to use another person's credentials or appears on a watchlist. These systems are more common now but still raise significant privacy concerns we'll address in section 10.
Be transparent about your visitor ID verification process. Post clear signage explaining:
- What identification you accept (driver's license, passport, national ID, corporate ID)
- You're collecting this information (security, compliance, insurance requirements)
- How you store the data and for how long
- Whether you use biometric scanning and their right to opt out
Always obtain explicit consent before scanning any identification document. Your visitor identity checking process should feel professional and respectful, never invasive or arbitrary.
Start Your Free Trial Today
Experience all the amazing functionalities of VizMan with our 14-day free trial. No commitment, full access to all features.
Register Now
5. Integrate Visitor Management System with Access Control & CCTV
VMS access control integration creates a unified picture of who's in your building and where they're allowed to go. When your systems communicate seamlessly, security gaps disappear.

Here's what unified security management looks like in practice:
When a visitor checks in at reception, your visitor management system immediately communicates with your access control system, creating a temporary credential valid only for today and only for approved areas. The visitor's badge now opens the elevator to the 5th floor where their meeting is, but won't open doors to the executive suite or IT server room.
Then comes door release integration that means your receptionist can remotely unlock the lobby door for a known visitor or trigger a lockdown if needed. Temporary credentials expire automatically at the scheduled end of the visit, so there's no risk of someone using yesterday's badge today.
Also, CCTV integration adds another security layer. If an incident occurs, you can immediately pull up video footage tagged with visitor information, dramatically reducing investigation time.
When someone badges into a restricted area they shouldn't access, multiple systems respond simultaneously: access denied at the door reader, alert sent to security staff, CCTV automatically focuses on that door, and incident logged in your audit trail.
6. Visitor Screening & Watchlists
Visitor screening means checking potential visitors against various lists before they ever reach your door. Your security watchlist check might include former employees terminated for cause, contractors with expired certifications, individuals with restraining orders against your staff, or anyone your organization has flagged as unwelcome.
Maintain an internal visitor blacklist. Document clearly why someone is on this list and who has authority to add or remove names. Regular reviews ensure the list stays current and legally defensible.
Background checks for visitors are standard in sensitive industries like defence contractors, pharmaceutical research, or financial institutions handling classified information. If your organization requires this level of visitor screening, integrate it into your pre-registration workflow so checks are completed before arrival.
AI-assisted screening tools can now cross-reference visitor names against multiple databases simultaneously, flagging potential matches in seconds rather than hours. These systems work in the background during pre-registration, giving security teams time to investigate before the visitor arrives.
Train your reception staff on how to handle a flagged entry with professionalism and safety:
- Never accuse or confront aggressively
- Use neutral language: "I need to verify some information"
- Involve a manager or security officer immediately
- Have a private area for sensitive conversations
- Know when to call security or police
The visitor screening process should work quietly in the background. Most visitors never know they've been screened. The system only alerts staff when it finds a match requiring human judgment.
7. Badge & Temporary Credential Management
Visitor badge printing should happen at check-in, ideally automated through your visitor management system. Modern systems print professional badges including photo, name, host name, visit date, and expiration time in seconds.
Visitor badges should be instantly recognizable to staff. Large text, clear photos, and prominent expiration information help anyone spot whether a badge is current and legitimate. Color-coded badges by visitor type make visual identification even faster.

Digital visitor badges displayed on smartphones work well for frequent visitors and contractors. The badge displays a QR code that changes periodically and can be scanned at door readers. Your badge system is only as strong as your organization's commitment to actually checking them.
Start Your Free Trial Today
Experience all the amazing functionalities of VizMan with our 14-day free trial. No commitment, full access to all features.
Register Now
8. Reception Staff Training & SOPs
Reception staff security training transforms your front desk team from administrative support into security professionals who happen to be friendly. This isn't about turning receptionists into security guards, but giving them the awareness, skills, and confidence to spot problems early.
Comprehensive front desk security training covers:
Threat recognition: What does suspicious behaviour actually look like? Someone nervously checked for cameras. A visitor who's overly interested in building layout. Someone attempting to bypass sign-in. Multiple people arriving separately but entering together. Social engineering attempts disguised as urgent delivery or maintenance requests.
De-escalation techniques: How to handle an angry visitor without escalating the situation. When someone becomes aggressive, trained receptionists use calm tones, acknowledge frustrations, offer solutions, and know exactly when to call for help.
Emergency response: What to do during a fire alarm, medical emergency, active threat, or natural disaster. Your receptionist emergency training should include their specific role in evacuation procedures and how to use panic buttons or silent alerts.
Security training for receptionists should happen during onboarding and through quarterly refresher sessions. Your front desk procedures should be documented in a clear incident response guide that sits at every reception station.
Make it a quick reference with tabs for different scenarios:
- Standard check-in procedures
- Visitor denied entry
- Medical emergency
- Fire/evacuation
- Aggressive visitor
- Suspicious package
- System failure (power out, network down)
Balance security with hospitality. The best receptionists make guests feel welcome while consistently enforcing policy.
Mandatory training for reception staff should include:
- Your organization's security policies and why they matter
- Hands-on practice with all technology systems
- Recognition of social engineering tactics and manipulation attempts
- Data privacy and compliance requirements (GDPR, local regulations)
- Conflict resolution and difficult conversation skills
- First aid and emergency response basics
Empower your reception team. Make clear they have full authority to politely deny entry to anyone who doesn't follow procedures, regardless of how important that person claims to be. Support them when they enforce policy correctly.
9. Emergency Readiness & Muster Lists
Emergency readiness is a legal requirement in most jurisdictions and an ethical obligation everywhere. Emergency evacuation procedures must account for every person on-site, employees and guests alike.
This is where your visitor management system proves its value. A digital visitor muster list shows in real-time exactly who checked in today and whether they've checked out. No guessing. No paper sign-in sheets that someone left at the front desk.

The emergency procedure should be this simple:
- Alarm sounds, everyone evacuates
- Fire warden at muster point pulls up the digital visitor log on their tablet or phone
- System shows all visitors currently on-site (checked in, not checked out)
- Each visitor's name appears with their host's name
- Fire warden confirms each visitor is accounted for
- Any missing person triggers immediate communication with emergency services
But the system only works if you've prepared properly.
Your employees know where to go. Visitors don't. Post evacuation maps prominently in all visitor areas. Train reception staff to briefly mention evacuation procedures during check-in for extended visits. Some organizations send automated SMS messages to all on-site visitors during emergencies with evacuation instructions.
Visitor Management Systems should have specific emergency evacuation features:
- One-click emergency status report showing current occupants
- Integration with mass notification systems to alert visitors via SMS
- Ability to mark individuals as safely evacuated in real-time
- Post-event reporting for emergency services and compliance
- Historical data showing who was on-site at the time of incident
Modern cloud-based systems enable coordination across multiple sites simultaneously. If you manage several locations, a centralized emergency dashboard shows occupancy and status for all buildings.
Don't forget special needs. Your visitor screening should flag anyone requiring assistance during evacuation (mobility limitations, visual or hearing impairments). Assign specific staff to assist those individuals, and document these assignments in your emergency procedures.
10. Data Privacy, Logging, Audits & Compliance
Data privacy compliance has gotten significantly stricter. GDPR in Europe, CCPA in California, and similar privacy laws worldwide mean you can't just collect visitor data casually and keep it forever. Enforcement has intensified in 2026, with regulators actively auditing visitor data handling practices.
Start with data minimization. Your privacy policy for visitors should explain exactly what information you collect and why. Don't collect more than you need. If you collect data for security purposes, you can't repurpose it for marketing without explicit consent. Be clear about your purposes and stick to them.
Implement a visitor data retention policy that makes sense for your needs while respecting privacy:
- Active visitor logs: Keep for the duration of visit
- Recent logs: Retain for 30-90 days for security investigations
- Historical logs: Archive for 1-7 years for compliance and legal holds
- Aged data: Automatically delete after retention period expires
Your visitor management software should auto-delete visitor records once they're past the retention threshold. Manual deletion is unreliable, automate it.
Visitor log audits serve multiple purposes. Regular audits help you:
- Verify your retention policy is working (old data actually gets deleted)
- Check that only authorized personnel access visitor data
- Ensure data accuracy and completeness
- Meet regulatory requirements for data processing accountability
- Identify unusual patterns that might indicate security issues
Conduct visitor record audits quarterly. Review access logs to see who's been viewing visitor data and why. Most access should be to reception staff during normal operations. If someone from an unrelated department accessed visitor logs, investigate why.
Visitor information security means encryption everywhere. Your visitor data encryption should cover:
- Data in transit (HTTPS for web access, encrypted API calls)
- Data at rest (encrypted database storage)
- Backup data (encrypted backup files)
- Archive data (encrypted long-term storage)
Limit access strictly. Not everyone in your organization needs to see visitor logs. Implement role-based access controls:
- Reception staff: Can view and edit current day's visitors
- Security personnel: Can view all current and recent visitors
- Compliance officers: Can run reports and audits
- Executives: Should probably have no access unless there's a specific business need
GDPR-compliant visitor management requires you to honour data subject rights:
- Right to access: Visitors can request their data
- Right to rectification: They can correct errors
- Right to erasure: They can request deletion (with exceptions for legal obligations)
- Right to data portability: They can request their data in machine-readable format
Build these capabilities into your system before someone exercises these rights. Scrambling to manually extract one person's data from your database creates risk and damages trust.
Start Your Free Trial Today
Experience all the amazing functionalities of VizMan with our 14-day free trial. No commitment, full access to all features.
Register Now
Bonus: Low-Cost & Quick Wins
Here are some quick reception security fixes you can implement immediately:
Physical layout improvements:
- Position your reception desk with clear sightlines to all entrances
- Add a cheap office security improvement: a wide-angle mirror to see blind spots
- Ensure the reception area is well-lit with no dark corners
- Install CCTV cameras near reception as a visible deterrent (even non-functional cameras improve behaviour)
- Lock away unattended visitor badges in a drawer when reception is unstaffed
Simple procedural changes:
- Create a visitor sign-in sheet (physical backup if your digital system fails)
- Train staff to always verify identity politely, even for regular visitors
- Display clear reception signage explaining check-in requirements
- Keep emergency contact numbers visible at reception
- Establish a buddy system where reception staff never work alone during high-risk times
Quick technology wins:
- Use a tablet for visitor sign-in with a simple form builder if you don't have a Visitor Management System yet
- Set up automatic email alerts when VIPs or flagged visitors check in
- Configure your security cameras to record motion-triggered footage, not continuous recording (saves storage and makes finding incidents easier)
- Use your existing badge printer to create color-coded visitor badges with just paper and design templates
Training that costs nothing:
- Run monthly 5-minute reception security tips sessions during team meetings
- Create a front desk quick-reference card with responses to common scenarios
- Practice emergency procedures every quarter
- Subscribe to industry security newsletters for awareness of new threats
Start with a low-cost office security foundation: clear policies, trained staff, and basic tools. Add sophisticated technology as your budget and needs grow.
Building a Security Culture That Actually Works
Office security in 2026 isn't really about the technology or the procedures we've covered. It's about culture. Real security happens when everyone, from the CEO to the intern, understands that front desk security protocols exist for everyone's protection. When leadership consistently follows the same check-in procedures they require of visitors, the message is clear: security matters here!
The reception area risk assessment you conduct today will be outdated next year. Threats evolve. Technology changes. Your workplace transforms. The best organizations don't build static security systems. They build adaptive ones that improve continuously.




